Tenable Identity Exposure-Protokolldateien
Wenn nach der GPO- und WMI-Consumer-Validierung immer noch keine Warnungen zu Indicators of Attack angezeigt werden, können Sie die internen Protokolle von Tenable Identity Exposure überprüfen.
-
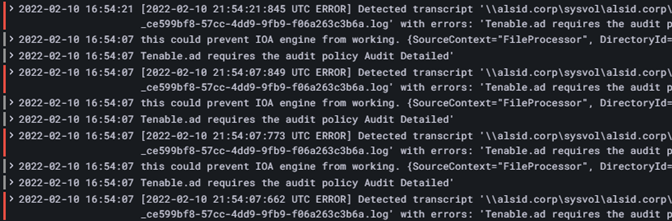
Suchen Sie im CETI-Protokoll nach der folgenden Fehlermeldung:
Kopieren[2022-02-22 22:23:27:570 UTC WARNING] Some domain controllers are not generating IOA events: 'CORP-DC'. {SourceContext="DirectoryEventToCetiAdObjectMessageMapper", DirectoryId=2, Dns="corp.bank.com", Host="10.10.20.10", Source=SYSVOL, Version="3.11.5"}
-
Wenn diese Meldung angezeigt wird, überprüfen Sie, ob die GPO-Einstellungen und der WMI-Consumer auf dem in der obigen Fehlermeldung aufgeführten Domänencontroller (DC) ausgeführt werden.
-
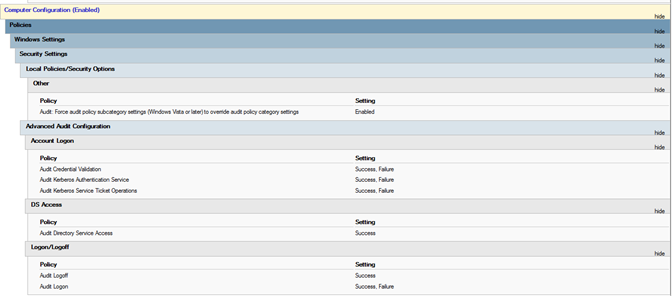
Wenn ein Fehler ähnlich dem folgenden angezeigt wird: „Tenable Identity Exposure requires the Audit Policy…“, überprüfen Sie Ihre vorhandenen GPOs, um sicherzustellen, dass Sie die erforderlichen Überwachungsrichtlinien nicht auf „Keine Überwachung“ festgelegt haben.
-
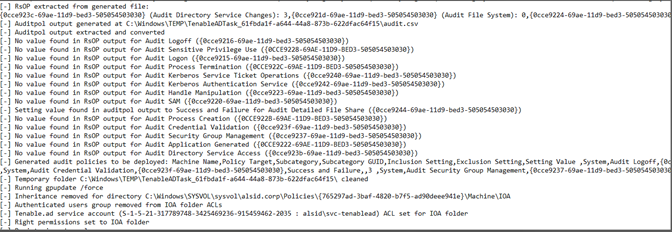
Wenn Sie eine Fehlermeldung mit folgendem Inhalt erhalten: „RSOP...“:
-
Überprüfen Sie die Überwachungsrichtlinien und sehen Sie sich die Transkriptdatei im SYSVOL-Ordner an, um festzustellen, ob während der Installation Probleme aufgetreten sind.
Cygni protokolliert den Angriff und listet die spezifische .gz-Datei auf, die Tenable Identity Exposure aufgerufen hat, um die Warnung zu generieren.
2022-03-15 11:39:31
[2022-03-15 15:39:30:759 UTC INFORMATION] Anomaly 'ControlAccess' has been raised for Indicator 'I-DCSync' and Event '110052' {SourceContext="AttackEngine", CodeName="I-DCSync", ProfileId=4, AdObjectId="5:\\\\alsid.corp\\sysvol\\alsid.corp\\Policies\\{08D6D98F-7455-464B-BBEC-23DE4BDF856C}\\Machine\\IOA\\dc-vm-10.0.17763-16_.gz", Event.Id=0, Version="3.16.0"}2022-03-15 11:40:31
[2022-03-15 15:40:31:490 UTC INFORMATION] Anomaly 'Logon' has been raised for Indicator 'I-GoldenTicket' and Event '110061' {SourceContext="AttackEngine", CodeName="I-GoldenTicket", ProfileId=3, AdObjectId="5:\\\\alsid.corp\\sysvol\\alsid.corp\\Policies\\{08D6D98F-7455-464B-BBEC-23DE4BDF856C}\\Machine\\IOA\\dc-vm-10.0.17763-16_.gz", Event.Id=0, Version="3.16.0"}022-03-15 12:47:09
[2022-03-15 16:47:09:811 UTC INFORMATION] Anomaly 'ProcessAccess' has been raised for Indicator 'I-ProcessInjectionLsass' and Event '115948' {SourceContext="AttackEngine", CodeName="I-ProcessInjectionLsass", ProfileId=1, AdObjectId="5:\\\\alsid.corp\\sysvol\\alsid.corp\\Policies\\{08D6D98F-7455-464B-BBEC-23DE4BDF856C}\\Machine\\IOA\\dc-vm-10.0.17763-16_.gz", Event.Id=0, Version="3.16.0"}2022-03-15 11:30:30
[2022-03-15 15:30:30:657 UTC INFORMATION] Anomaly 'ControlAccess' has been raised for Indicator 'I-DCShadow' and Event '109948' {SourceContext="AttackEngine", CodeName="I-DCShadow", ProfileId=4, AdObjectId="5:\\\\alsid.corp\\sysvol\\alsid.corp\\Policies\\{08D6D98F-7455-464B-BBEC-23DE4BDF856C}\\Machine\\IOA\\dc-vm-10.0.17763-16_.gz", Event.Id=0, Version="3.16.0"}2022-03-15 08:02:11
[2022-03-15 12:02:11:231 UTC INFORMATION] Anomaly 'An account failed to log on' has been raised for Indicator 'I-BruteForce' and Event '109082' {SourceContext="AttackEngine", CodeName="I-BruteForce", ProfileId=6, AdObjectId="3:\\\\alsid.corp\\sysvol\\alsid.corp\\Policies\\{765297AD-3BAF-4820-B7F5-AD90DEEE941E}\\Machine\\IOA\\dc-vm-10.0.17763-8_.gz", Event.Id=0, Version="3.16.0"}2022-03-15 12:39:43
[2022-03-15 16:39:43:793 UTC INFORMATION] Anomaly 'An account failed to log on.' has been raised for Indicator 'I-PasswordSpraying' and Event '115067' {SourceContext="AttackEngine", CodeName="I-PasswordSpraying", ProfileId=4, AdObjectId="5:\\\\alsid.corp\\sysvol\\alsid.corp\\Policies\\{08D6D98F-7455-464B-BBEC-23DE4BDF856C}\\Machine\\IOA\\dc-vm-10.0.17763-16_.gz", Event.Id=0, Version="3.16.0"}2022-03-15 12:43:02
[2022-03-15 16:43:02:737 UTC INFORMATION] Anomaly 'PetitPotamEFSError' has been raised for Indicator 'I-PetitPotam' and Event '115844' {SourceContext="AttackEngine", CodeName="I-PetitPotam", ProfileId=4, AdObjectId="5:\\\\alsid.corp\\sysvol\\alsid.corp\\Policies\\{08D6D98F-7455-464B-BBEC-23DE4BDF856C}\\Machine\\IOA\\dc-vm-10.0.17763-16_.gz", Event.Id=0, Version="3.16.0"}022-03-15 12:55:31
[2022-03-15 16:55:31:638 UTC INFORMATION] Anomaly 'LocalAdmin enumeration (BloodHound/SharpHound). Version 2016+' has been raised for Indicator 'I-ReconAdminsEnum' and Event '116085' {SourceContext="AttackEngine", CodeName="I-ReconAdminsEnum", ProfileId=4, AdObjectId="5:\\\\alsid.corp\\sysvol\\alsid.corp\\Policies\\{08D6D98F-7455-464B-BBEC-23DE4BDF856C}\\Machine\\IOA\\dc-vm-10.0.17763-16_.gz", Event.Id=0, Version="3.16.0"}022-03-15 12:51:30
[2022-03-15 16:51:30:236 UTC INFORMATION] Anomaly 'Kerberos TGS requested on honey account' has been raised for Indicator 'I-Kerberoasting' and Event '116013' {SourceContext="AttackEngine", CodeName="I-Kerberoasting", ProfileId=3, AdObjectId="5:\\\\alsid.corp\\sysvol\\alsid.corp\\Policies\\{08D6D98F-7455-464B-BBEC-23DE4BDF856C}\\Machine\\IOA\\dc-vm-10.0.17763-16_.gz", Event.Id=0, Version="3.16.0"}2022-03-15 12:03:51
[2022-03-15 16:03:50:949 UTC INFORMATION] Anomaly 'Shadow copy created on 2012 and above' has been raised for Indicator 'I-NtdsExtraction' and Event '111168' {SourceContext="AttackEngine", CodeName="I-NtdsExtraction", ProfileId=4, AdObjectId="5:\\\\alsid.corp\\sysvol\\alsid.corp\\Policies\\{08D6D98F-7455-464B-BBEC-23DE4BDF856C}\\Machine\\IOA\\dc-vm-10.0.17763-16_.gz", Event.Id=0, Version="3.16.0"}Die folgenden Protokolleinträge bestätigen, dass Cephei Angriffe notiert. Der Schlüsselwert ist die attackTypeID, die die Art des Angriffs angibt. Diese können Sie für die Korrelation mit den Cygni-Einträgen verwenden:
2022-03-15 11:39:52
2022-03-15T15:39:52.037023041Z stdout F [2022-03-15 15:39:52:035 UTC INFORMATION] [Equuleus] POST http://equuleus:3004/attacks/write responded 204 in 32.16 ms : Request Body={"timestamp":"1647358722449","directoryId":5,"profileId":4,"attackTypeId":1,"count":1} {SourceContext="Equuleus", Version="3.16.0"}2022-03-15 11:40:52
2022-03-15T15:40:52.084931986Z stdout F [2022-03-15 15:40:52:084 UTC INFORMATION] [Equuleus] POST http://equuleus:3004/attacks/write responded 204 in 24.6607 ms : Request Body={"timestamp":"1647358773608","directoryId":5,"profileId":4,"attackTypeId":2,"count":1} {SourceContext="Equuleus", Version="3.16.0"}2022-03-15 12:47:52
2022-03-15T16:47:52.29927328Z stdout F [2022-03-15 16:47:52:298 UTC INFORMATION] [Equuleus] POST http://equuleus:3004/attacks/write responded 204 in 35.7532 ms : Request Body={"timestamp":"1647362812784","directoryId":5,"profileId":1,"attackTypeId":3,"count":2} {SourceContext="Equuleus", Version="3.16.0"}2022-03-15 11:30:52
2022-03-15T15:30:51.949399295Z stdout F [2022-03-15 15:30:51:944 UTC INFORMATION] [Equuleus] POST http://equuleus:3004/attacks/write responded 204 in 24.2605 ms : Request Body={"timestamp":"1647358182800","directoryId":5,"profileId":3,"attackTypeId":4,"count":1} {SourceContext="Equuleus", Version="3.16.0"}
2022-03-15 08:02:54
2022-03-15T12:02:54.698814039Z stdout F [2022-03-15 12:02:54:698 UTC INFORMATION] [Equuleus] POST http://equuleus:3004/attacks/write responded 204 in 30.7623 ms : Request Body={"timestamp":"1647345728023","directoryId":3,"profileId":6,"attackTypeId":5,"count":1} {SourceContext="Equuleus", Version="3.16.0"}2022-03-15 12:39:52
2022-03-15T16:39:52.187309945Z stdout F [2022-03-15 16:39:52:186 UTC INFORMATION] [Equuleus] POST http://equuleus:3004/attacks/write responded 204 in 21.9422 ms : Request Body={"timestamp":"1647362356837","directoryId":5,"profileId":4,"attackTypeId":6,"count":1} {SourceContext="Equuleus", Version="3.16.0"}022-03-15 12:43:52
2022-03-15T16:43:52.226125918Z stdout F [2022-03-15 16:43:52:223 UTC INFORMATION] [Equuleus] POST http://equuleus:3004/attacks/write responded 204 in 15.8402 ms : Request Body={"timestamp":"1647362570534","directoryId":5,"profileId":1,"attackTypeId":7,"count":1} {SourceContext="Equuleus", Version="3.16.0"}2022-03-15 12:55:52
2022-03-15T16:55:52.399889635Z stdout F [2022-03-15 16:55:52:399 UTC INFORMATION] [Equuleus] POST http://equuleus:3004/attacks/write responded 204 in 40.6632 ms : Request Body={"timestamp":"1647363305295","directoryId":5,"profileId":4,"attackTypeId":8,"count":1} {SourceContext="Equuleus", Version="3.16.0"}
2022-03-15 12:51:52
2022-03-15T16:51:52.352432644Z stdout F [2022-03-15 16:51:52:351 UTC INFORMATION] [Equuleus] POST http://equuleus:3004/attacks/write responded 204 in 21.0547 ms : Request Body={"timestamp":"1647363026345","directoryId":5,"profileId":4,"attackTypeId":10,"count":1} {SourceContext="Equuleus", Version="3.16.0"}
022-03-15 12:03:52
2022-03-15T16:03:52.137547488Z stdout F [2022-03-15 16:03:52:137 UTC INFORMATION] [Equuleus] POST http://equuleus:3004/attacks/write responded 204 in 13.0304 ms : Request Body={"timestamp":"1647360224606","directoryId":5,"profileId":4,"attackTypeId":11,"count":1} {SourceContext="Equuleus", Version="3.16.0"}Sie sollten den folgenden Eintrag sehen:
[2022-03-15T14:04:39.151Z] INFO: server/4016 on WIN-UQRSCEN0CI3: Message received from MQ: attack-alert (namespace=electra)
[2022-03-15T14:04:39.151Z] INFO: server/4016 on WIN-UQRSCEN0CI3: Message received from MQ: attack-alert (namespace=electra)
[2022-03-15T14:04:39.168Z] INFO: server/4016 on WIN-UQRSCEN0CI3: Sending ws message to listeners. alertIoA (namespace=electra)Sie sollten den folgenden Eintrag sehen:
022-03-15T14:04:39.150Z] INFO: server/4988 on WIN-UQRSCEN0CI3: KAPTEYN get /attack-alerts/2010 200 122 - 7ms (namespace=hapi)
[2022-03-15T14:04:39.165Z] INFO: server/4988 on WIN-UQRSCEN0CI3: notifyAttackAndAttackAlertCreation success { attackId: 2011 } (namespace=eridanis)
[2022-03-15T14:04:39.170Z] INFO: server/4988 on WIN-UQRSCEN0CI3: KAPTEYN get /attack-alerts/2011 200 122 - 6ms (namespace=hapi)